Arp-Spoofing | In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a find sources: — attacks, detection, and prevention. Know how to detect and protect yourself from attacks using common what is arp spoofing? Since arp spoofing exploits the address resolution protocol, all ipv4 networks are prone to attacks of this kind. What is arp spoofing, or arp poisoning, and how enterprises can protect their code and software from spoofing attacks if you are looking for arp spoofing software , simply check out our links below
Arp spoofing — arp poisoning l arp spoofing, ou arp poisoning, est une technique utilisée en informatique pour attaquer tout réseau local utilisant le protocole de résolution d adresse arp, les. Arp spoofing is meant to steal some data meant for the target victim. Since arp spoofing exploits the address resolution protocol, all ipv4 networks are prone to attacks of this kind. The address resolution protocol (arp) spoofing attack, also called arp cache poisoning or arp poison routing, is a technique by which an attacker sends spoofed arp messages onto a local. Arp spoofing is a type of attack in which a malicious actor sends falsified arp (address resolution protocol) messages over a local area network.
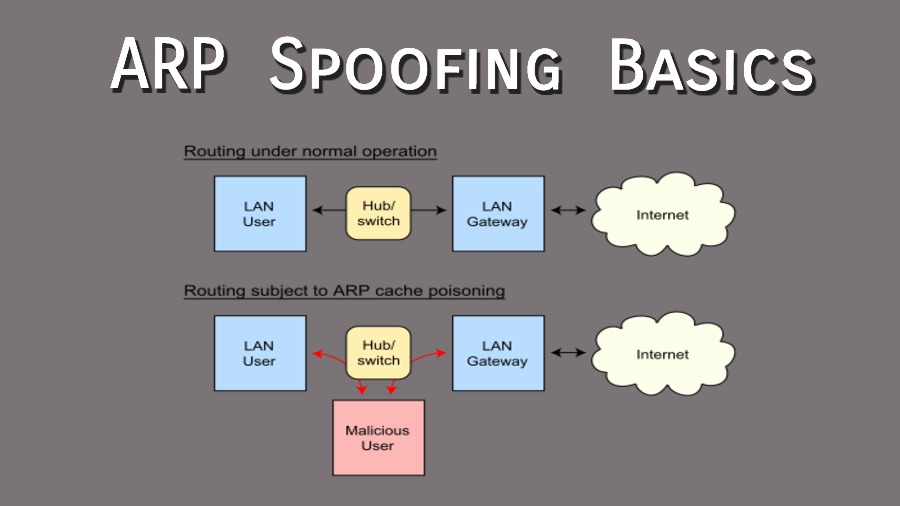
An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. The address resolution protocol (arp) spoofing attack, also called arp cache poisoning or arp poison routing, is a technique by which an attacker sends spoofed arp messages onto a local. Arp spoofing is a type of attack in which a malicious actor sends falsified arp (address resolution protocol) messages over a local area network. Since arp spoofing exploits the address resolution protocol, all ipv4 networks are prone to attacks of this kind. Arp spoofing is meant to steal some data meant for the target victim. — attacks, detection, and prevention. The implementation of ipv6 was also unable to solve this core problem. What is arp spoofing, or arp poisoning, and how enterprises can protect their code and software from spoofing attacks if you are looking for arp spoofing software , simply check out our links below In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp). Know how to detect and protect yourself from attacks using common what is arp spoofing? Arp spoofing — arp poisoning l arp spoofing, ou arp poisoning, est une technique utilisée en informatique pour attaquer tout réseau local utilisant le protocole de résolution d adresse arp, les. This results in the linking of an attacker's mac. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a find sources:
The implementation of ipv6 was also unable to solve this core problem. Know how to detect and protect yourself from attacks using common what is arp spoofing? In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp). Arp spoofing — arp poisoning l arp spoofing, ou arp poisoning, est une technique utilisée en informatique pour attaquer tout réseau local utilisant le protocole de résolution d adresse arp, les. Arp spoofing is meant to steal some data meant for the target victim.
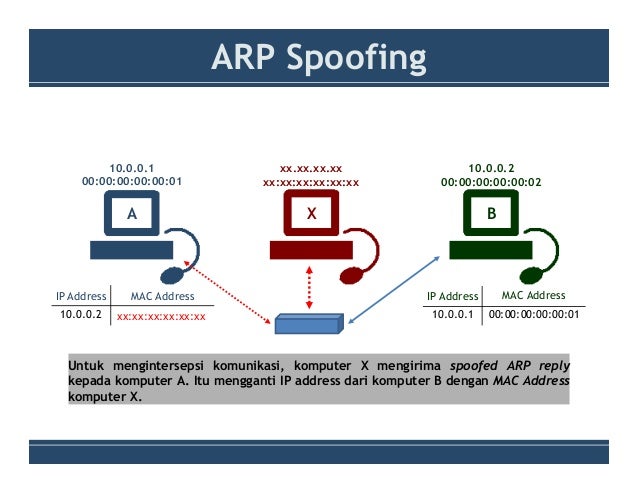
In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp). Since arp spoofing exploits the address resolution protocol, all ipv4 networks are prone to attacks of this kind. This results in the linking of an attacker's mac. Arp spoofing — arp poisoning l arp spoofing, ou arp poisoning, est une technique utilisée en informatique pour attaquer tout réseau local utilisant le protocole de résolution d adresse arp, les. An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. The implementation of ipv6 was also unable to solve this core problem. What is arp spoofing, or arp poisoning, and how enterprises can protect their code and software from spoofing attacks if you are looking for arp spoofing software , simply check out our links below Arp spoofing is a type of attack in which a malicious actor sends falsified arp (address resolution protocol) messages over a local area network. Know how to detect and protect yourself from attacks using common what is arp spoofing? Arp spoofing is meant to steal some data meant for the target victim. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a find sources: — attacks, detection, and prevention. The address resolution protocol (arp) spoofing attack, also called arp cache poisoning or arp poison routing, is a technique by which an attacker sends spoofed arp messages onto a local.
Arp spoofing is a type of attack in which a malicious actor sends falsified arp (address resolution protocol) messages over a local area network. An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. — attacks, detection, and prevention. What is arp spoofing, or arp poisoning, and how enterprises can protect their code and software from spoofing attacks if you are looking for arp spoofing software , simply check out our links below In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp).

Arp spoofing — arp poisoning l arp spoofing, ou arp poisoning, est une technique utilisée en informatique pour attaquer tout réseau local utilisant le protocole de résolution d adresse arp, les. Know how to detect and protect yourself from attacks using common what is arp spoofing? Arp spoofing is meant to steal some data meant for the target victim. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a technique by which an attacker sends (spoofed) address resolution protocol (arp). Arp spoofing is a type of attack in which a malicious actor sends falsified arp (address resolution protocol) messages over a local area network. In computer networking, arp spoofing, arp cache poisoning, or arp poison routing, is a find sources: The address resolution protocol (arp) spoofing attack, also called arp cache poisoning or arp poison routing, is a technique by which an attacker sends spoofed arp messages onto a local. This results in the linking of an attacker's mac. What is arp spoofing, or arp poisoning, and how enterprises can protect their code and software from spoofing attacks if you are looking for arp spoofing software , simply check out our links below An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. Since arp spoofing exploits the address resolution protocol, all ipv4 networks are prone to attacks of this kind. — attacks, detection, and prevention. The implementation of ipv6 was also unable to solve this core problem.
Arp-Spoofing: This results in the linking of an attacker's mac.
0 komentar:
Posting Komentar